Here are my 9 Ds of Cloud Computing - D for Differences (which I produced for my Information Security FS 2013 presentation).
Cloud computing is a form of sourcing / outsourcing, of IT resources. But -
- Disassociation - separation of the physical from the logical is common (eg physical access to data vs logical, often remote, access); and so is separation of ownership vs control vs use
- Diverse supply chain (hardware, software, services); even layers of services are possible, eg:
- Don’t always know or have influence over all suppliers - customers are in quite a different position from traditional outsourcing, it's often a 'cloud of unknowing' for customers, who may not always be able to find out full information about sub-providers etc, or be able to negotiate providers' standard contract terms
- ‘Direction of travel’ is reversed - if using sub-providers. In traditional outsourcing, a customer may go out to tender with details of the service it seeks, discuss the position with several shortlisted potential providers and narrow it down; the provider finds sub-contractors to help it deliver the service requested by the customer. In cloud, SaaS (or even PaaS) providers often build their services on top of pre-existing IaaS or PaaS services, then offer their services to customers, ie the 'direction of travel' is the opposite from that in traditional outsourcing; and opportunities for customising the service are limited
- DIY - cloud involves the self-service use by customers of IT hardware / software infrastructure, offered as services, such as software applications in SaaS or virtual servers in IaaS; the provider doesn't actively process data for customers
- Design – the design of the individual service (as well as user measures eg encryption, which the service may or may not facilitate) will affect the extent to which the provider has access to user data, including encrypted data. Key access is also critical - if the user has encrypted the data but the provider can access the key, it can still access intelligible data. Conversely if the provider has encrypted user data and manages the key securely, any sub-provider(s) may not be able to access intelligible user data.
- Data – cloud-processed data are often:
- distributed, which overlaps with the following, that cloud data may be
- divided into chunks / fragments which are stored, and sometimes processed, separately
- duplicated (multiple replicas or copies of data may be taken, perhaps to different geographical locations, for backup/business continuity purposes),
- 'deleted' in different ways - deletion may only delete 'pointers' to data rather than scrubbing underlying data, which are gradually over-written over time; even any scrubbing of data may be achieved to different degrees of deletion (and security), and duplicates of data stored in backups, etc may not get deleted
- Dependence – on shared, third party resources - including the customer's Internet connectivity
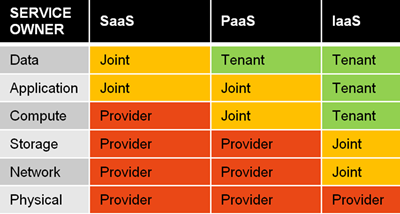
- Degrees of control, eg regarding security issues, differ with the situation - it's not one size fits all (see table below)
Table © Cloud Security Alliance reproduced with permission
See also: previous post about the 12 Cs of Cloud Computing (here's the full SCL article: The 12 Cs of Cloud Computing: A Culinary Confection), including explanations of SaaS, PaaS and IaaS for those not familiar with the terms.